In today’s digital era, scams and fraudulent lines of action seem to be thriving, taking on new and improved forms, exploiting users’ concerns and fears on technology. The fraudulent pop-up message ‘Your Computer May be at Risk’ is one such rising scam that appears on your computer screen alerting you of security threats present and demanding actions to be taken urgently. Usually, these messages are delivered as part of a scam related to tech support. The motive of threat actors is either monetary gain by making users pay for some service or planting malware on victims’ devices. This article explores how this scam works and provides guidelines on protecting yourself from it.
The ‘Your Computer May Be at Risk’ scam normally starts with an urgent-looking pop-up message declaring that your computer is infected with viruses, malware, or other security threats. The message typically compels you to call a toll-free number or click on a link for immediate support to fix the threat. Attackers carrying out the scam exploit the fear of users to create a sense of urgency expecting the victims to act impulsively.
Victimized users calling the number or following the link are connected with a fake tech support agent who claims to be from a reputable company, such as Microsoft or Apple. The agent will further try to stress the degree of risk of the situation and offer to resolve the issue by accessing the user’s computer remotely. When it reaches this point, the scam may follow one of the below courses:
Below are some proactive measures to be followed to protect yourself from the ‘Your Computer May Be at Risk’ scam:
Follow the link below for instructions to remove unwanted ads. This is just one of the many articles available on the web to help clean up the situation. You can discover and read more about resolving the ‘Your Computer May be at Risk’ popup.
https://support.google.com/chrome/answer/2765944?hl=en&co=GENIE.Platform%3DDesktop
The “Your Computer May Be at Risk” scam preys on people’s fears of cyber threats and their lack of technical knowledge. By staying informed and following best practices for online security, you can protect yourself from falling victim to such scams. Remember that legitimate tech support will never use fear tactics or demand immediate payment, and if something seems suspicious, take the time to independently verify the situation before taking any action.
Modern AI tools have witnessed significant advancements in recent years, driven by breakthroughs in machine learning techniques and computing power. These advancements in machine learning techniques and computing power have synergistically propelled the field of AI forward. They have led to breakthroughs in various applications. As AI tools continue to advance, we can expect further innovations that will drive progress in numerous domains, benefiting industries and society as a whole.
AI tools, or artificial intelligence tools, refer to software applications or platforms that utilize artificial intelligence techniques to perform specific tasks or assist users in various ways. These tools leverage technologies such as machine learning, natural language processing, computer vision, and more to automate processes, analyze data, make predictions, and provide intelligent recommendations. With these attributes, the use of AI has widely proliferated in the following areas in recent times;
In summary, the tool collects and analyzes data to process the outcome. In the process, the tool is also capable of “learning” or “training” itself based on the collected data in order to provide better answers for future queries. This is a critical point where sensitive information can leak into the wrong hands. The information that we feed into AI tools is used for further enhancements and is no longer treated as secure. Therefore, it’s imperative that we do not feed any sensitive or business-critical information into AI tools, as they can be used to train the AI model resulting in it being let out at large and appearing at unwanted places, such as in other’s queries.
AI tools are exposed to and used by everyone at large. A massive volume of data is continuously being exchanged via these tools. Unknown to most users, this information is vulnerable to a lot of threats. Some of these threats can be categorized as below:
AI tools often require access to large amounts of data for training and analysis. This data can contain sensitive and personal information, making it a prime target for hackers or unauthorized access. If the data is not properly protected, it can lead to privacy breaches and potential misuse of personal information.
Adversarial attacks involve manipulating AI systems by intentionally feeding them misleading or malicious input data. This can result in AI systems making incorrect or harmful decisions, potentially leading to security breaches or system vulnerabilities. Adversarial attacks are a significant concern in areas such as image recognition, natural language processing, and autonomous vehicles.
AI models are trained using datasets, and if an attacker can inject malicious or manipulated data during the training process, it can compromise the integrity and security of the AI system. This can lead to biased or inaccurate predictions, unauthorized access, or other malicious activities.
AI tools often have complex architectures and interfaces that can be susceptible to unauthorized access or control. If an attacker gains unauthorized access, they can manipulate the AI system’s behavior, steal sensitive information, or disrupt its functioning.
AI tools learn from historical data, and if the training data is biased or reflects discriminatory patterns, the AI models can perpetuate those biases or discrimination in their predictions. This can lead to unfair or discriminatory outcomes, posing ethical and legal risks.
AI tools often rely on various components, libraries, or external services provided by third parties. If these dependencies are not properly vetted or secured, they can introduce vulnerabilities or backdoors into the AI system, which can be exploited by attackers.
Research [1] shows some existing insights about information exposure to a generative AI tool like chatGTP. It was discovered that a 44% increase in GenAI usage over the last three months alone. Despite this growth, only an average of 19% of an organization’s employees currently utilize GenAI tools. Below graph shows how users had exposed information to AI tools.
Another research [2] shows user adaptation for AI tools like chatGTP and how they exposed information to tools.
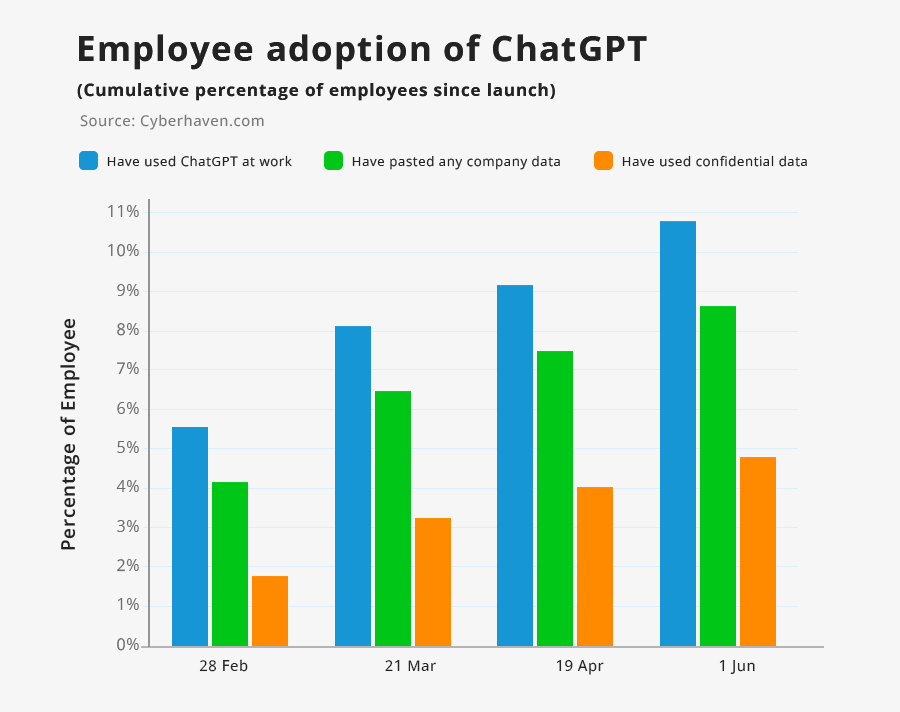
The graph above indicates how users have relied on AI tools to get their work done in recent times.
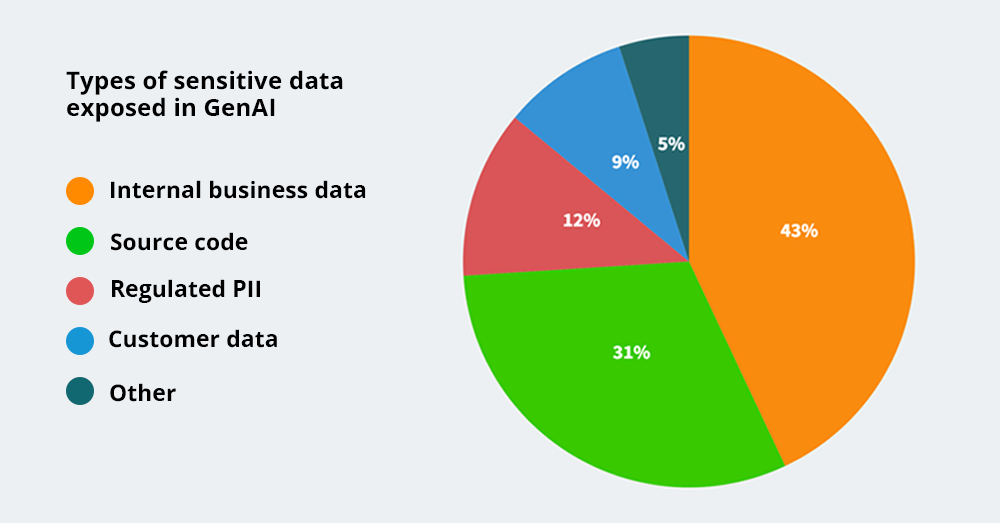
The graph below shows how they have inadvertently exposed different types of information to AI tools.

Both these research results [1][2] show the information security threats that could arise via AI tools.
Therefore, User Awareness and Education is the key factor to control information security threats. Promote user awareness and education regarding security best practices. By promoting user awareness and education, individuals can become empowered stakeholders in the AI ecosystem, thereby promoting responsible, ethical, and beneficial outcomes for individuals and society. As part of security education, we should provide clear instructions on the safe usage of AI tools and potential security risks. Encourage users to report any security concerns or vulnerabilities they discover. eBuilder Security provides managed information security awareness training through its Complorer training platform. Read more on Complorer via www.complorer.com.
Furthering our commitment to being the forerunner in providing the best of cybersecurity solutions, eBuilder Security now introduces employee training through Complorer – an automated Security Awareness Training product offered with the Managed Services model for safeguarding the lifeblood of your organization, your employees.
Security vulnerabilities are concealed in all systems, across multiple devices over different platforms through varying roles that engage with the organization. A single loophole in the process, a minor flaw within the security system, and/or a simple shortcoming on the part of the human resource could have the potential to trigger a detrimental security breach that compromises your system in its entirety.
Even with the best of systemized security measures in place, this means that you are still susceptible to inadvertent actions of the human component of your setup. In that sense, the whole of your security organization is only as good as the naivest clickbait victim in your organization. Not if you have taken appropriate measures to brace your staff duly with due vigilance though.
Your security awareness program requires constant surveillance, adherence to compliance requirements, continuous assessment, and maintaining cybersecurity best practices. Internally, this translates into dedicated personnel working on multiple processes consuming considerable amounts of time and resources. Further, not all organizations are equipped with the right expertise that the dynamic volatile landscape of cybersecurity demands.
eBuilder Security’s Complorer helps you combat all of the above quandaries in a single strike.
Treading the precarious waters of cyberspace in the post-pandemic era, we are maneuvering with an increase in remote work, cloud usage, AI, and IoT inherent technologies that expand the potential scope for cyberattacks by many fold.
As cited by Forbes’ Most Critical Cybersecurity Trends of 2023, phishing and social engineering attacks remain alarmingly prevalent in 2023 as well, making employee awareness and training a crucial part of the risk mitigation plan.
Filling the void in the dearth of smart options available for organizations, eBuilder Security presents Complorer, a convenient awareness training program carefully designed to guide employees with minimal disruptions to routine operations.
So you’ve got mail. The red-alerted company-wide “for your attention” email on security awareness from last week still needs to be read in full. Scurrying your focus through the most important activities for the day is a Herculean task much underrated now. In the age of perpetual information overload, it helps to have just the right information you need, filtered by your role. That’s what we do with our role-based nano training.
Complorer Security Awareness comprises training material tailored for different employee roles such as that of the receptionist, HR personnel, customer representative, executive etc. on top of the regular awareness training as a whole. Each of the specific roles is faced with different types of risks as their interactions with people and systems vary based on the tasks they carry out. Unassuming threats too loom about high and wide in varied guises within these same routine tasks.
Complorer presents specific awareness training that helps each of the job roles with additional training material adhering to compliance requirements like NIS2. With specifically tailored training, each job role is then able to identify the distinct threats they are exposed to in their regular work.
Phishing and social engineering attacks manipulate individuals through deceit and often seep through security filters in place directly approaching individuals via emails, and social media, as responses to posts, legitimate services, advertisements, etc.
Complorer’s automated phishing testing and targeted attack simulations help your employees learn how to navigate through many a bait in digital waters unscathed.
eBuilder Security’s Complorer is a comprehensive training service providing hands-on training for the employees while unburdening yourself from training administration and management, i.e., freeing yourself to proceed with your routine operations unhindered.
Designed by the best of expertise in the domain, we have incorporated effective visual and auditory learning techniques into our training modules, with the content available in different formats covering visual, audio, and text based learning methods.
Well-acquainted with the regional demand for local language driven training, our sessions are also available in multiple languages.
The training process and its progress can conveniently be tracked at a glance via our dashboards. Complete with reporting functionality, dashboards track compliance and depict vital statistics of the training progress daily.

Offering you the best of expertise in the field at highly competitive and affordable prices, Complorer powered by eBuilder Security presents you with scalable training plans that meet your requirements just right.
With its time tested expertise in the domain, eBuilder Security prides itself in excelling at shielding enterprises from falling prey to vicious cybercrimes, preventing cyberattacks before they ever happen.
Get in touch with us today and start your security awareness training journey with Complorer.